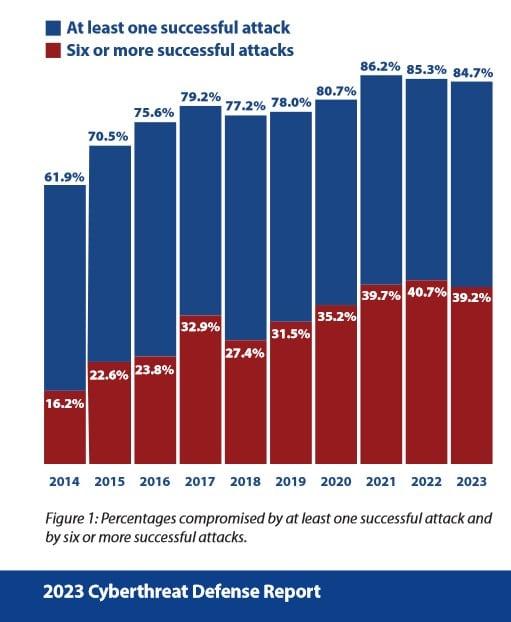
In today’s hyper-connected world, cybercrime is evolving at a dizzying pace, constantly challenging our understanding of digital security. From ransomware attacks to data breaches, the threats seem to multiply and morph overnight, leaving individuals and organizations scrambling to keep up. But what exactly is driving these changes, and where is cybercrime headed next? In this blog, we’ll dive deep into the emerging trends shaping the future of cybercrime, exploring the tactics hackers are adopting and what it means for all of us navigating the digital age. Ready to unravel the mysteries behind tomorrow’s cyber threats? Let’s get started.
Table of Contents
- Emerging Cybercrime Techniques That Are Changing the Game
- How AI and Automation Are Fueling Cybercriminals’ Arsenal
- Protecting Yourself Against Sophisticated Digital Threats
- Future-Proofing Your Security Strategy with Proactive Measures
- Final Thoughts
Emerging Cybercrime Techniques That Are Changing the Game
In the ever-evolving landscape of cybercrime, hackers are no longer satisfied with traditional tactics. They’ve begun leveraging AI-driven phishing schemes that craft hyper-personalized messages, making malicious attempts almost indistinguishable from genuine communications. Another game-changer is the rise of deepfake technology—cybercriminals are now using AI-generated videos and audio clips to impersonate trusted figures and manipulate both individuals and organizations into divulging sensitive information or authorizing fraudulent transactions.
Moreover, the underground economy has expanded with innovations like cryptojacking, where hackers hijack computing power to mine cryptocurrency stealthily, often going unnoticed for months. Then there’s the increasing exploitation of Internet of Things (IoT) vulnerabilities, turning everyday smart devices into entry points for large-scale attacks. Key tactics include:
- Botnet formations utilizing unsecured IoT devices to launch massive Distributed Denial of Service (DDoS) attacks
- Manipulation of smart home systems for ransomware schemes
- Use of autonomous malware that adapts and evolves to bypass traditional security methods
How AI and Automation Are Fueling Cybercriminals’ Arsenal
Artificial intelligence and automation have become double-edged swords in the cyber world. While they promise efficiency and innovation, these technologies also empower cybercriminals with unprecedented capabilities. AI-driven tools enable hackers to execute sophisticated phishing campaigns with messages that mirror human communication flawlessly, making detection nearly impossible. Automation scripts can scan for vulnerabilities at lightning speed, launching attacks across multiple targets simultaneously without the constraints of human limitations. These advancements not only increase the volume of cyberattacks but also their precision, turning ordinary cybercrime into a meticulously orchestrated endeavor.
What makes this evolution even more daunting is how cyber adversaries are integrating machine learning algorithms to adapt in real-time, learning from each failed attempt to improve future breach strategies. This dynamic adaptability transforms static defense mechanisms into obsolete relics. Key factors fueling this digital arms race include:
- Automated credential stuffing that exploits breached data at scale;
- AI-generated deepfakes used for social engineering and identity fraud;
- Intelligent malware that modifies its code to evade detection systems;
- Rapid exploit development powered by AI-driven vulnerability discovery.
As the toolkit of cybercriminals expands with the infusion of AI and automation, cybersecurity strategies must evolve faster than ever to shield against this new breed of threats.
Protecting Yourself Against Sophisticated Digital Threats
In an era where cybercriminals employ ever-evolving tactics, staying vigilant requires more than just basic antivirus software. Implementing a multi-layered defense strategy is crucial to outsmart these sophisticated attackers. This involves regularly updating software to patch vulnerabilities, using strong, unique passwords combined with multi-factor authentication (MFA), and keeping a close eye on unusual account activities. Furthermore, it’s essential to cultivate a cybersecurity mindset—not just for IT teams but for all users—to recognize social engineering schemes and phishing attempts before they can cause damage.
Beyond technical solutions, empowerment through education is a powerful shield. Training programs and simulations can arm individuals and organizations with the knowledge to detect subtle clues in fraudulent emails or suspicious links. Always remember, the human element remains the first line of defense. Key practices to embed in your digital routine include:
- Verifying email sources before clicking links
- Regularly backing up important data offline
- Encrypting sensitive communications and files
- Limiting permissions on digital accounts to the minimum necessary
Future-Proofing Your Security Strategy with Proactive Measures
In an era where cyber threats evolve at lightning speed, waiting for breaches to happen is no longer an option. Security strategies must shift from reactive to proactive defense mechanisms that anticipate and neutralize risks before they escalate. This involves integrating advanced threat intelligence, leveraging AI-powered analytics, and adopting continuous monitoring systems that adapt as attackers innovate. Organizations that embed these dynamic tools into their security frameworks not only mitigate current vulnerabilities but also build resilience against the unknown challenges of tomorrow.
Embracing a future-ready posture also means investing in foundational practices that empower teams and technology alike. Consider prioritizing the following elements for a robust, adaptable security strategy:
- Regular vulnerability assessments to identify emerging weaknesses promptly.
- Employee cybersecurity training to turn the human factor into a formidable defense layer.
- Zero-trust architectures ensuring no implicit trust within digital environments.
- Collaboration with industry forums to stay ahead of evolving threat landscapes.
These proactive measures, when combined, craft a security ecosystem that doesn’t just respond to cybercrime — it anticipates, adapts, and thrives in the face of it.
Final Thoughts
As we continue to navigate the ever-evolving digital landscape, staying curious and vigilant about emerging cybercrime trends is more important than ever. The threats are growing smarter, but so are the defenses—and the opportunities for innovation are endless. What’s next in this ongoing battle? Only time will tell, but one thing’s certain: by understanding these trends today, we can better prepare for the challenges of tomorrow. So keep your eyes open, stay informed, and let’s unravel the mysteries of cybercrime together. The digital age is just getting started.