
An American-Israeli national named Osei Morrell has been arrested in Israel for his alleged involvement in exploiting the Nomad bridge smart-contract in August 2022 that allowed hackers to siphon $190 million.
Blockchain intelligence platform TRM Labs supplied key information to international law enforcement authorities, leading to the identification of Morrell, who is believed to have played a central role in what is one of the largest hacks in DeFi history.
“The suspect, American-Israeli dual national Osei Morrell, was arrested in Jerusalem by Israeli police working in coordination with the DOJ, the FBI, and Interpol,” explained TRM Labs.
According to the blockchain intelligence firm, Morell will soon be extradited to the United Statesas the legal precedures have already been approved.
Morrell’s links to Nomad Bridge hack
The Nomad bridge is a cross-chain communication standard that allows users to transfer assets between different blockchains.
On August 1, 2022, attackers exploited a critical vulnerability introduced in an update to its Replica smart contract, specifically in the ‘process() function.’
Though the contract was supposed to verify message proofs before releasing funds, a misconfiguration allowed any message with a correct root hash to be accepted, even if the underlying proof was invalid.
Once a single attacker figured out the flaw, the exploit method was quickly picked up by hundreds of other wallets, as it consisted in simply copy-pasting a specific transaction format.
This “mob-style” attack led to a chaotic and decentralized looting of the bridge, draining over $190 million in ETH, USDC, WBTC, and ERC-20 tokens.
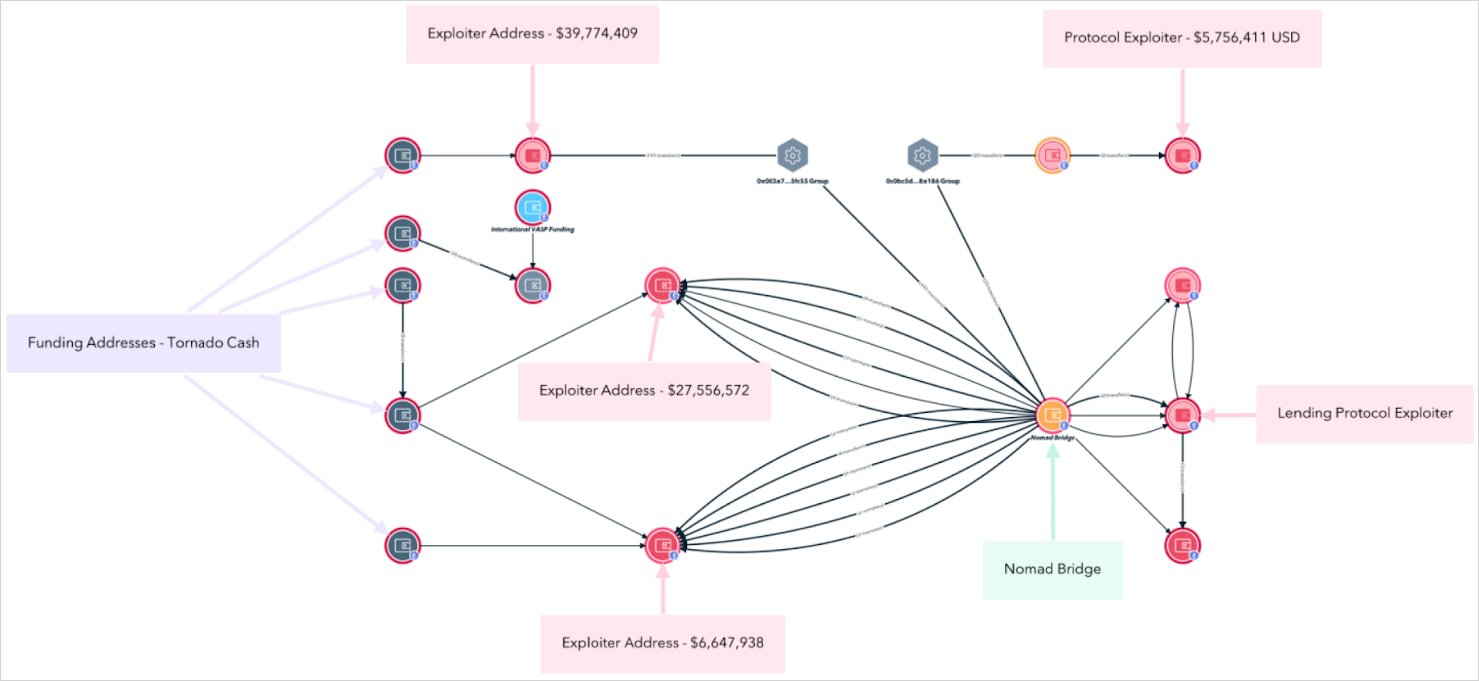
Source: TRM Labs
TRM Labs comments that the vulnerability was very easy to leverage, so even people with no hacking skills or deep blockchain knowledge joined in the exploitation. However, experienced North Korean actors were also implicated.
Osei Morrell is not believed to have written or initiated the exploit code itself, but TRM Labs says he “played a central role,” and evidence suggests he conspired with others to launder large amounts of funds stolen during the exploit.
Wallets linked to Morrell received stolen assets within hours of the bridge being drained, suggesting close coordination with early attackers.
TMR Labs’ data shows that Morrell used ‘chain-hopping’ to move the stolen tokens across various blockchains, the Tornado Cash mixer to obfuscate the origin of the funds, and swapped ETH into the privacy-boosting Monero (XMR) and Dash.
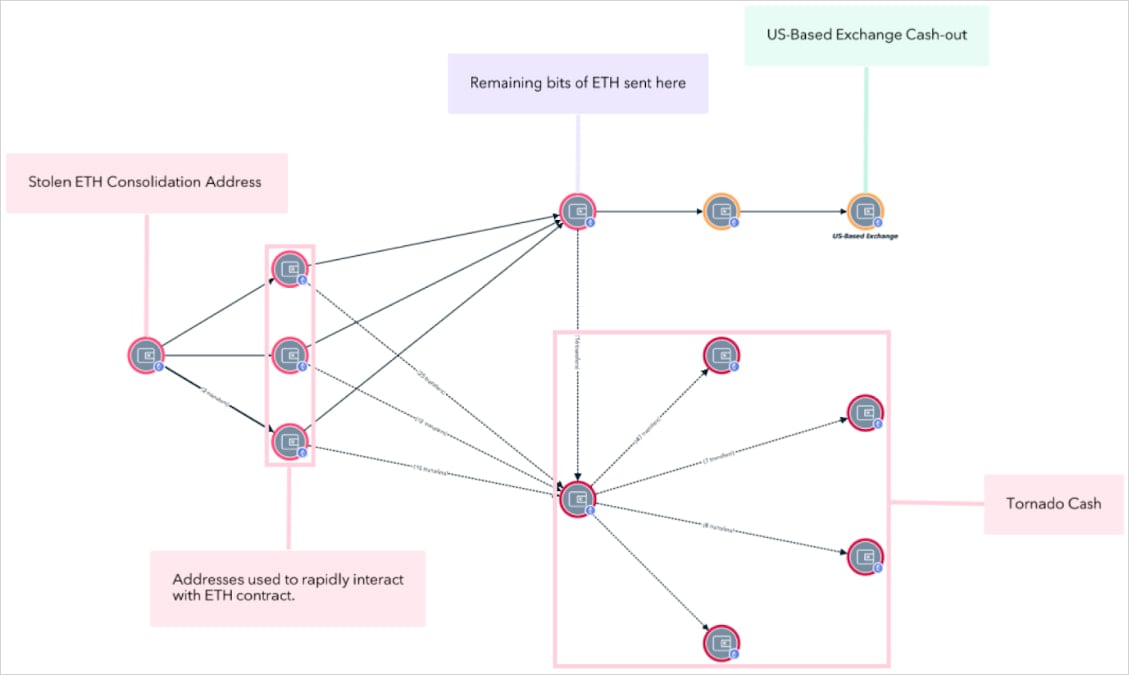
Source: TRM Labs
To cash out the proceeds, he used non-custodial exchanges, OTC brokers, and offshore bank accounts tied to fake or opaque legal entities, and also converted some crypto to fiat through providers with no KYC standards.
Despite all the obfuscation efforts and the time that has passed since these events, blockchain transaction analysis still yielded enough clues to uncover Morrell’s identity, resulting in his arrest.
Morrell’s arrest follows that of another suspected hacker, a Russian-Israeli citizen named Alexander Gurevich, who was caught on May 1st at the Ben Gurion airport in Tel Aviv using documents under a new name, Alexander Block, he had officially changed.
According to prosecutors, Gurevich exploited the Nomad bridge flaw and withdrew about $2.89 million in digital tokens. This was followed by others finding the issue and leveraging it to siphon assets.
Jerusalem Post reports that on August 4, 2022, Gurevich contacted Nomad’s Chief Technology Officer and admitted he had been probing Nomad for weaknesses, apologizing for the trouble and later demanding a $500,000 reward for identifying the vulnerability.

Based on an analysis of 14M malicious actions, discover the top 10 MITRE ATT&CK techniques behind 93% of attacks and how to defend against them.

