Earlier this week, the FBI urged folks to bin aging routers vulnerable to hijacking, citing ongoing attacks linked to TheMoon malware. In a related move, the US Department of Justice unsealed indictments against four foreign nationals accused of running a long-running proxy-for-hire network that exploited outdated routers to funnel criminal traffic.
In a FLASH bulletin [PDF] on Wednesday, the FBI warned that aging routers from Linksys, Ericsson, and Cisco, commonly found in homes and small businesses, were being actively targeted by cybercriminals.
These devices, long past their update window, were compromised and made available for sale as part of a criminal proxy network marketed through the 5socks and Anyproxy domains. The botnet provided anonymity to malicious users and enabled a range of cybercrime, including distributed denial of service (DDoS) attacks, according to federal investigators and security researchers.
Here are the dusty old routers you need to watch out for:
- Linksys E1200, E2500, E1000, E4200, E1500, E300, E3200, E1550 and WRT320N, WRT310N, WRT610N kit
- The Ericsson Cradlepoint E100 router
- The Cisco Valet M10
A DoJ indictment issued on Friday offered more details on how the botnets allegedly operated. The operators charged between $9.95 and $110 per month for access to what they claimed were over 7,000 residential proxies, the indictment claims. Prosecutors believe the scheme pulled in more than $46 million, with the website boasting it had been “Working since 2004!”
Not anymore, since the domain running the attacks has been seized in what the Feds are calling Operation Moonlander.
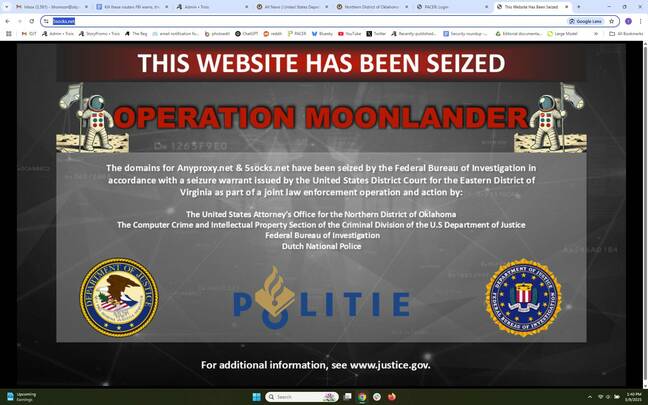
You’ve been pwned- Click to enlarge
A separate FBI PSA issued Wednesday described a wave of router infections using TheMoon malware, consistent with the timing of the domain seizure takedown. TheMoon, first identified in 2014, is notorious for infecting routers via open ports and vulnerable scripts. In March 2024, it compromised over 6,000 Asus routers in under 72 hours as part of a proxy-building campaign.
“TheMoon does not require a password to infect routers; it scans for open ports and sends a command to a vulnerable script,” the FBI PSA explains. “The malware contacts the command and control (C2) server and the C2 server responds with instructions, which may include instructing the infected machine to scan for other vulnerable routers to spread the infection and expand the network.”
Three Russian nationals – Alexey Viktorovich Chertkov, 37, Kirill Vladimirovich Morozov, 41, Aleksandr Aleksandrovich Shishkin, 36 – and a Kazakhstani associate Dmitriy Rubtsov, 38 – were named in the Friday indictment. Chertkov and Rubtsov were also charged with providing false registration information when signing up the domains used to operate the proxy services.
The indictments are a result of a combined operation between European and US law enforcement, as well as with support from Lumen’s Black Lotus Labs. The operators exploited outdated routers and maintained a relatively low operational footprint – despite advertising access to thousands of proxies – to avoid detection.
“The botnet operators claim that they maintain a daily population of over 7,000 proxies. Based on Black Lotus Labs’ telemetry, we can see an average of about 1,000 weekly active proxies in over 80 countries, however we believe their true bot population is less than advertised to potential users,” the security shop said. ®

